Key Takeaways:
Enterprise app security protects sensitive data, prevents breaches, and keeps critical business operations running without disruption across teams, regions, and integrated systems.
Security-by-design reduces long-term costs by identifying risks early, minimizing rework, and preventing expensive incidents tied to downtime, compliance failures, or data loss.
Strong API security and access control close common attack paths, protecting interconnected systems from unauthorized access and large-scale lateral breaches.
Continuous monitoring and regular testing enable faster threat detection, quicker response, and stronger operational resilience as applications scale and evolve.
Future-ready enterprise apps rely on cloud-native security, DevSecOps, and zero-trust models to manage growing complexity without sacrificing performance or compliance.
JPLoft helps businesses build secure, scalable enterprise applications by embedding security into architecture, development, and compliance from day one.
Enterprise applications handle sensitive business data, support critical operations, and serve thousands of users across global networks, making them prime targets for cyberattacks.
Therefore, the question arises, “What are the best enterprise app security practices to follow?”
Organizations must adopt security-by-design principles, implement continuous monitoring, encrypt data at rest and in transit, secure APIs and integrations, conduct regular security testing, and maintain strict compliance audits.
With data breaches costing enterprises millions in financial losses and reputational damage, proactive security isn't optional; it's essential for business survival.
This comprehensive guide explores enterprise app security fundamentals, covering the four pillars of protection, critical security components, essential practices for 2026, and actionable strategies to safeguard your enterprise applications effectively.
Let’s begin with the right practices.
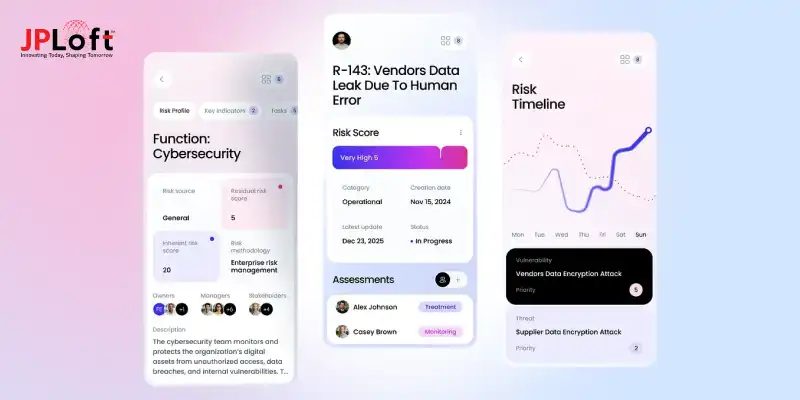
What Is Enterprise App Security?
Enterprise application security is a comprehensive strategy that uses processes, tools, and policies for protecting large, critical business apps and software from any kind of cyber threats.
It is a set of processes, tools, and strategies that are used for protecting large-scale applications.
This is one of the important practices for protecting the large-scale, business-critical software systems from cyber threats across the entire software lifecycle.
It further helps to focus on safeguarding sensitive enterprise data via a secure architecture, access control, and compliance measures.
Why Enterprise App Security Matters for Modern Businesses?
There are many reasons why to opt for security for an enterprise app, such as business continuity risks, competitive and market pressures, regulatory and legal liability exposure, talent acquisition, supply chain, and ecosystem trust.
Well, if you are focusing on building an enterprise app, then learning about the reasons why enterprise app security matters is important.
Let’s figure it all out in this section:
►Competitive & Market Pressures
Security has evolved from a compliance checkbox to a competitive differentiator in the vendor space selection processes.
This is the key factor that directly affects customer trust, sales cycles, and market expansion. The security certification, such as SOC 2 have become a compulsion for the enterprises.
►Regulatory and Legal Liability Exposure
The security failures in the enterprise apps are one of the most important reasons to invest in an enterprise app security program.
The cumulative GDPR fines have reached approximately to €5.88 billion, which highlights continuous enforcement of the data protection laws and the rise of financial repercussions for non-compliance. Hence, investing is one of the impotant determinant.
►Maintains Operational Continuity
An app security program can help you to detect any kind of threats and vulnerabilities that might harm the overall business and apps.
Along with this, the security incidents can disrupt the core business workflows, cause downtime, and impact revenue generation.
Furthermore, it ensures data integrity, enforces secure access, and enables rapid recovery, all through measures such as zero-trust principles, continuous monitoring, and secure development.
►Talent Acquisition and Retention Challenges
Security maturity has become a prime factor in attracting the top engineering talent who view security practices as a critical factor in mobile app development and for enterprises.
The enterprises with weak programs often struggle to find senior developers who are well concerned about their professional development reputation and effective career prospects.
But what if you do not follow these reasons for security for an enterprise app? Are there any risks aligned with the same/
Well, let's examine the risks involved in an enterprise app in the following section.
What are the Risks Involved in an Enterprise App?
There are certain risks involved in enterprise apps, such as data breaches, insider threats, supply chain attacks, unclear requirements, budget overruns, timeline overruns, integration issues, and skill gaps.
Let’s discuss them all in detail below.
Risk 1: Data Breaches and Unauthorized Access
The central apps, such as an enterprise app, are the prime targets for the attackers, risking sensitive data.
This can even lead to financial losses, operational disruptions, reputational damage, loss of customer trust, and legal penalties.
Risk 2: Insider Threats
The insider threats originate from trusted individuals who can be employees, contractors, or business partners, who can use the unauthorised access to cause harm to the enterprise, intentionally.
Hence, protecting the enterprise from such insider threats is important.
Risk 3: Supply-Chain Attacks
The vulnerabilities in open-source libraries or third-party components can compromise the core systems of an enterprise app.
These are the major enterprise app security concerns that might affect thousands of organizations, as seen in events like SolarWinds.
Risk 4: Scalability and Performance Risks
As the usage of the enterprise app grows, the poorly secured architecture may fail.
A slow security measure can result in financial loss that might further impact the overall performance issues of the app. Hence, the security of the app is very significant.
RIsk 5: API and Integration Vulnerabilities
Enterprise apps rely heavily on third-party APIs and integrations. Insecure endpoints or poor validation can open gateways for attacks across connected systems.
This might lead to weak authentication, data overexposure, and reliance on the third-parties, creating vulnerabilities for data breaches.
Now, let's switch to the next section, stating the four pillars to secure an enterprise app in the following section.
Four Pillars to Secure an Enterprise App
Here are the four working pillars to be considered for an enterprise app. Here, the four pillars can be coverage, efficiency, accuracy, and continuity.
Well, you might have noted that including the security parameter can increase the overall cost to build an enterprise app.
Now, let's evaluate the complete four pillars to secure an enterprise app, below.
Pillar 1: Coverage
It is one of the well-worn truths that defenders need to secure everything, while the attackers find only one weakness in the complete system.
Ideally, the application security program should ensure that you know all the attack points, and should be well aware that you have left with no known gaps for the attackers when it comes to an enterprise app.
Pillar 2: Efficiency
To be efficient, your app must be tested properly and needs to be remediated at the speed of development of the app.
Any kind of sizable organization or enterprise needs to test its application. Additionally, you must build complex applications and also deploy the functionalities effectively.
Pillar 3: Accuracy
This is the third pillar when it comes to the enterprise app security protocol.
Accuracy is the foundational pillar that operates alongside reliability and the security programs.
It is important to ensure that the system is trustworthy, actionable, and capable of supporting the businesses.
Pillar 4: Continuity
Continuity is all about keeping going no matter what, even if you are confident that you have full security testing coverage of your entire web application environment, each test run gives you the snapshotof the current security posture of your app in the enterprise industry.
Now, proceeding wth the pillars of security in an enterprise app. Let's find out the different components in the following section.
Components of an Enterprise App Security
The diversified components include secure architecture and design, comprehensive security testing, and many more.
Let’s learn about each of the components of enterprise app security below.
Component 1: Secure Software Development Lifecycle (SSDLC)
An SSDLC incorporates security into the entire application development lifecycle, which starts from the requirement gathering process, the coding phase, the design phase, and then to the development phase.
The regular updates within an enterprise application security program help the teams to adopt the secure coding standards as the foundation of the product creation.
Component 2: Effective Architecture and Design
The security of an app begins with a solid foundation. Here, designing applications with principles such as least privilege and defense in depth reduces the frequency of cyber attacks.
Conducting threat modeling can secure the software development standards that help to prevent vulnerabilities before they enter production.
Component 3: Continuous Monitoring and Incident Response
The threats can emerge at any time, making real-time monitoring essential.
Here, you need an automated data collection, real-time analysis, network monitoring, and threat intelligence integration.
You should opt for reporting and alerting when it comes to enterprise app security, which comprises regular monitoring and incident response.
Component 4: Patch Management and Vulnerability Disclosure
Regularly applying patches and updates can address known vulnerabilities before they can be exploited.
Additionally, maintaining a vulnerability disclosure program can encourage ethical reporting, which furthermore helps organizations to stay ahead of any kind of emerging threats.
Now, let's proceed with the practices in this guide to enterprise app security.
10 Enterprise App Security Practices to Cover in 2026
The diversified enterprise app security practices can adopt a security-by-design approach, encrypting data at rest and in transit, securing APIs and integrations, enabling continuous monitoring, and many more.
Let’s figure out the complete list in this section.
1. Perform Comprehensive Risk Assessment
This is the prime step when you think of mobile app security practices. Here, you should be able to conduct an effective and comprehensive risk assessment initiative.
Begin a thorough evaluation of potential threats, regulatory requirements, and data sensitivity for shaping the enterprise application security.
Here, you should evaluate what kind of potential errors and risks might occur in the future. You can include risk matrices, weighted scoring models, and a quantitative model.
These will help you to identify the diversified types of risk assessment protocols, and then to take action accordingly.
2. Adopting the Security by Design Approach
Adopting the security by design approach refers to embedding security in the app from the very start through integrating security experts into the SDLC, conducting early modeling, threat analysis, and defining the security requirements
This is performed through cultivating a security-centric culture and training.
Here, you need to involve the security architects and perform threat modeling to identify the threats early.
3. Data Encryption Anywhere
Data encryption is an important practice for securing an enterprise app, because it transforms the sensitive data into unreliable code, helps to protect the confidentiality and integrity from different malware, and any unauthorized access anywhere.
Here, the core benefits of data encryption in the enterprise app is it helps to maintain confidentiality and integrity. This helps in meeting the strict requirements and regulations of the app via HIPAA and PCI DSS regulations.
4. Secure Third-party Integration
Securing the third-party integration is one of the important enterprise app security practices to be considered that is all about identifying the third-party apps and then securing their synchronization with the enterprise app.
You should note that exposure to third-party and supply chain security management increases exposure to supply chain attacks, which is worsened by poor visibility.
Hence, you can maintain a detailed inventory for all types of components by using the generate software bill of materials (SBOMs).
5. Integrate Security into DevOps
The traditional security practices can create friction in the fast-paced DevOps environments, with old tools and processes.
Here, you should include the shift-left security protocol by adopting tools like SAST and DAST, that too directly in the development systems.
To strengthen the pp security, you should consider the architecture of the application. It is vital to use security-as-code frameworks. This will help you to embed the security controls in the infrastructure.
6. Cloud-Native Security Management and Controls
Cloud-native security management uses methods such as DevSecOps, Zero Trust, and IAM that help to protect the data through continuous monitoring and APIs.
It helps to reduce risks that are unique to cloud architecture better than legacy tools.
Additionally, you can adopt services like Istio for enforcing the centralized security policies and to encrypt inter-service traffic.
With these security practices for an enterprise app, you can improve the cloud-native security management across the platform.
7. Implement Continuous Monitoring Initiative
The enterprise web app security practices do requires continuous systems monitoring for identifying and detecting threats as they arise.
When you integrate these capabilities into your enterprise app, it results in a fast response and helps to foster trust among users.
Now, you should automate processes through streamlining routine tasks such as scanning and compliance checks to reduce human error.
Along with this, you should use automated solutions such as SIEM, IDS, or vulnerability scanners for gathering crucial data for your enterprise app.
8. Conduct Regular Security Testing
It is an enterprise app development myth that testing should be conduct in the end of the app development procedure.
If you want your app to be secured from the very beginning, it is essential to automate processes and to conduct the testing process along with SDLC (software development life cycle).
Additionally, you should conduct training for the enterprise app, and you need to educate employees on their role in maintaining security.
9. Perform Compliance Audit
You should perform a compliance audit at least once a month to check what the recent regulations and practices fall under your enterprise app that need to be followed.
Updating the enterprise app according to compliance and regulations is a crucial activity to sustain in the marketplace.
It is important to design audit logs, data retention rules, and access reports early so the compliance doesn’t become a last-minute scramble.
10. Scale Security Across Distributed Development Teams
The distributed teams are often seen to lack the consisten security practices, which further results in delays in responses.
Therefore, you need to implement the security champions with each of the items to provide localized security guidance and expertise.
Along with this, you should automate the security gates within CI/CD pipelines for enforcing the policies regardless of team location.
You need to adopt a standardized application security guide for the role-based training to help the developers to stay aligned and consistent.
Challenges in Integrating a Security Program in an Enterprise App
Are you aware of the challenges of an enterprise app? Well, you will find that one of them is the integration of security protocols in an enterprise app.
And, when you decide to adopt or implement the security protocol in an enterprise app, it is essential to know the related challenges.
Let’s discover the challenges in integrating a security program into an enterprise app. Hence, let's discuss them all below.
Challenge 1: Complex Legacy System Integration
Many enterprises rely on outdated systems that were never designed for modern APIs or cloud environments.
Integrating new apps with legacy infrastructure often requires custom connectors, data transformation, and careful migration planning. This increases implementation time, cost, and risk.
Challenge 2: Data Security and Access Control Alignment
Different systems follow different security standards and access policies.
Aligning authentication, authorization, and data-sharing rules across platforms can create gaps if not planned carefully.
Inconsistent controls increase the risk of data leakage and unauthorized access.
Challenge 3: Scalability and Performance Constraints
As user loads and data volumes grow, integrations can become bottlenecks. Poorly optimized integrations may slow down core workflows and degrade user experience.
Scalability must be built into both the app and connected systems from the start.
Challenge 4: Compliance and Regulatory Complexity
Enterprise apps often operate across regions with varying data protection laws. Ensuring every integrated system meets compliance requirements adds significant complexity.
A single non-compliant integration can expose the entire enterprise to legal risk.
Challenge 5: Third-party Dependency Risk
Reliance on external vendors, APIs, or platforms introduces availability and security risks. Changes, outages, or vulnerabilities in third-party systems can disrupt operations.
Continuous monitoring and vendor risk management are essential.
Challenge 6: Change Management and User Adoption
Even well-integrated apps fail if teams resist change. Lack of training, unclear workflows, or poor communication can slow adoption.
Successful integration requires aligning technology with people and processes.
Connect with JPLoft to Build a Secure Enterprise App
Enterprise applications power critical business operations, manage sensitive data, and support large user bases across teams and regions. As complexity increases, security can no longer be treated as an add-on.
It must be embedded into architecture, workflows, and integrations from the very beginning. A secure enterprise app protects business continuity, ensures compliance, and builds long-term trust with users and stakeholders.
This is where JPLoft makes a difference. As an experienced enterprise app development company, JPLoft designs and builds secure, scalable enterprise applications tailored to real business needs.
From security-first architecture and compliance alignment to secure APIs and continuous monitoring, our teams help organizations build enterprise apps that are resilient, future-ready, and built to scale with confidence.
Conclusion
Enterprise application security is no longer optional. It's a business imperative that directly impacts competitive advantage, regulatory compliance, and operational continuity.
From secure architecture and continuous monitoring to API protection and compliance audits, implementing comprehensive security practices protects your organization from evolving cyber threats while building stakeholder trust.
The four pillars of coverage, efficiency, accuracy, and continuity provide a structured framework for maintaining robust security postures.
By adopting security-by-design principles, encrypting data everywhere, and integrating security into DevOps workflows, enterprises can build resilient applications that scale confidently.
Partner with experienced developers who prioritize security from day one to ensure your enterprise app remains protected, compliant, and future-ready.
FAQs
Enterprise app security is a comprehensive strategy using processes, tools, and policies to protect large-scale, business-critical applications from cyber threats throughout the entire software lifecycle. It encompasses secure architecture, access control, data encryption, continuous monitoring, and compliance measures to safeguard sensitive enterprise data.
Enterprise app security protects against financial losses, reputational damage, and regulatory penalties while ensuring operational continuity. It has become a competitive differentiator affecting customer trust, talent acquisition, and market expansion. Strong security programs are essential for vendor selection, compliance requirements, and maintaining stakeholder confidence.
The four pillars are coverage (securing all attack points), efficiency (testing and remediation at development speed), accuracy (reliable and actionable security systems), and continuity (maintaining an ongoing security posture). These pillars ensure comprehensive protection, rapid threat response, trustworthy security programs, and sustained resilience against evolving threats.
Major risks include data breaches and unauthorized access, insider threats from trusted individuals, supply chain attacks through third-party components, API vulnerabilities, scalability issues affecting performance, and integration weaknesses. These threats can cause financial losses, operational disruptions, reputational damage, and legal penalties if not properly addressed.
Essential practices include conducting comprehensive risk assessments, adopting security-by-design approaches, implementing data encryption everywhere, securing third-party integrations, integrating security into DevOps workflows, enabling continuous monitoring, performing regular security testing, conducting compliance audits, and scaling security across distributed development teams for comprehensive protection.











Share this blog